After The Breach, Get Ready for the Next One

Almost every week we learn that another company, government or non-governmental organisation has suffered a data breach. The way in which systems are built in this current age means that there is much less of a focus on creating solid, well-defended systems than there is on acquiring new users and getting a product out there. The technology sector’s obsession with data, tracking, analytics and conversion funnels has fuelled these disasters. Software security is relegated beneath the relentless focus on growth and engagement.
As cryptographer and security expert Bruce Schneier said in his brilliant book Click Here to Kill Everybody:
Big companies with few competitors don’t have much incentive to improve the security of their products, because users have no alternative; they either buy a product—security warts and all—or go without.
It is unlikely that the services that you use online, both those paid and unpaid, will change their ways swiftly enough for you to not worry about data breaches. By all means vote with your feet, complain, and nudge where possible, but we are going to outline here some useful steps in order to protect yourself against these breaches before they happen. We will also offer up a process for diagnosing whether you are already a victim, and the actions that you can take after that discovery.
Good Practices Before
Whenever signing up for a new service, ask yourself a range of questions:
- Do I really need this? Obviously, if the answer to this is no and you decide not to use the service then the risk of data loss is gone.
- Does this service need real details? Many services can be used pseudonymously and/or attached to throwaway Voice Over IP (VOIP) phone numbers. Services such as 33mail (an example, not a recommendation) can help by offering you the option of creating alias emails for new services.
- Do I need to install anything, or can this be accessed in my browser? Apps can be granted problematic permissions when installed on mobile devices, just as software installed on a computer can also collect things that you don’t want it to. A well-tuned browser is a better tool for accessing services than an app built and maintained on the service’s terms.
Remember they can only lose what you give them; if you appear in a breach with a fake name and an alias email address then it doesn’t really affect you. Would-be social engineering attackers and identity thieves cannot do much with fake information.
Checking If You’ve Been Compromised
The gold standard for checking leaked data is haveibeenpwned; any website other than that would require a decent amount of research and social proofing before we would recommend putting your real email address or phone number into it. Other services exist but beware that they could just be a clone that is harvesting information. This being said, if the phone number was a throwaway VOIP number or you were putting in an alias email, you would probably consider this to be less risky, because the information is fake or not directly linked to you in the way that your real number and actual email address are.
To check if you’ve been pwned you just need to enter your email of phone number into the box on the website. If you’ve had one email address for a long time, it is very likely that it will turn up in some breached data. It is also very possible that you will see this screen:
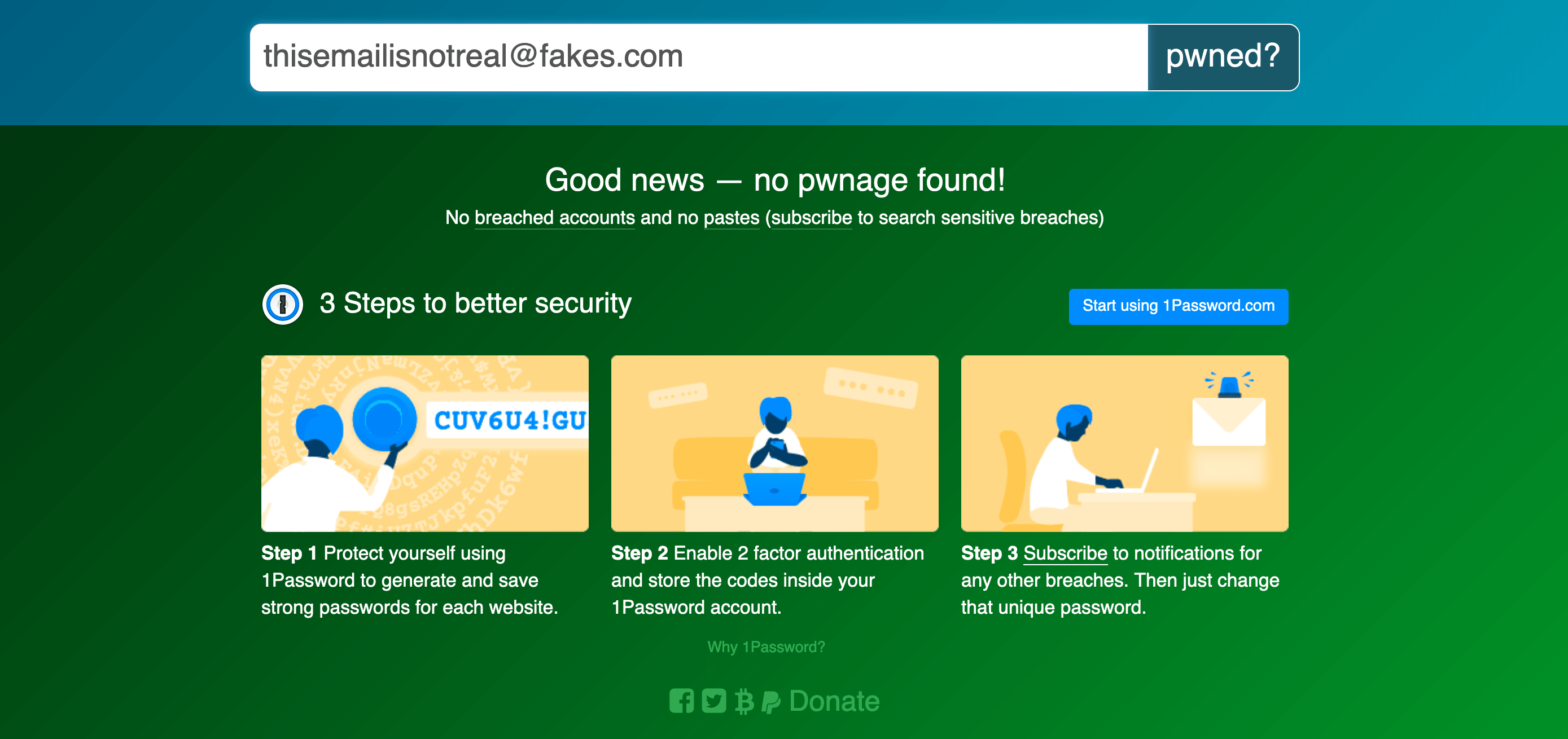
If so, well done, remember to check back some time in the future, and to keep going with whatever privacy and security checks and processes you already have in place. For a lot of you that will not be what happens though...
What To Do If You Have Been Pwned
For a lot of you, inserting an email address or phone number into the box will result in this screen:
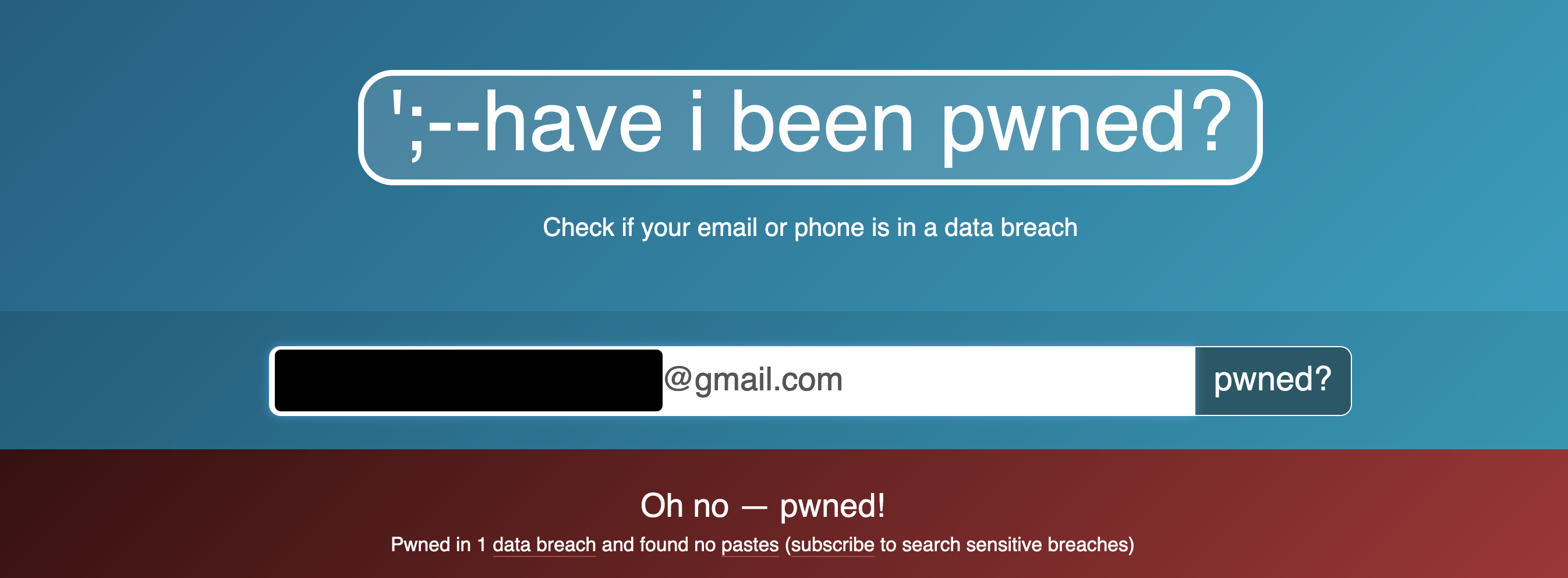
The email address above is from a longtime Gmail account and all the passwords from breached accounts have been changed and were different from each other - the damage could have been so much worse. It’s one case where Gmail (for once), with its excellent spam filter, is a blessing...
In general these are steps we would recommend if you’ve been pwned:
- Change the password that is associated with any account that has been breached, and change the password on any other account, breached or not, that uses this same password.
- Go to the email address in question and check your recovery questions. Quite frequently these can be things that can be gained through social engineering attacks i.e. someone getting in touch with someone who knows you and pretending to be an authority figure or service representative in order to garner data.
- If you don’t have one, use a password manager that allows you to generate strong unique passwords for every new service so that when one is breached, you only have to change one password to be back to a better level of security.
- Use secure recovery answers. If your email address can be recovered via your mother’s maiden name and she uses that on Facebook where you are publicly friends with her, then that recovery question is essentially useless. The best way to approach security/recovery questions is to give answers that are memorable/recorded in a secure database but that are not true.
- Keep your eyes open for spam, phishing, and text/call-based attacks (if the leaked data includes your phone number). A breached database containing your name, phone number, and where you bank is a prime case of lost information that can be used against you. Once you’ve discovered that details are in a breach, keep that in mind when interacting with people and services.
Stay Safe
The knowledge that breach databases like haveibeenpwned arm you with is invaluable. Unfortunately we live in a world with data harvesting, lax security, underwhelming compliance, and tepid enforcement.
Keep in mind that non-disclosure and leveraging services that do not collect this kind of data is the simplest and most effective form of defence. For example, if you want to search anonymously, and without any tracking or data harvesting, you know where we are.